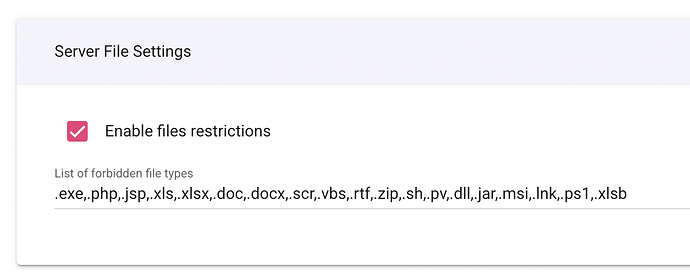
At present, malicious scripts or other malicious file types can be uploaded to the backend via any form ‘upload’ button.
This leaves Treepl/WebInOne vulnerable and has the potential to allow hackers to access personal CMS data collected via forms. This is a serious threat and must be resolved as data security becomes an increasingly high priority due to the huge number of breaches we hear of or experience on other high profile platforms.
A South Korean client recently had a security breach and data leak in their Australian database. Jobs were lost and the agency was cut. They are now putting all their agencies in all countries through a series of penetration tests to ensure security protocols are in place. Including my agency in New Zealand. I am the only supplier of theirs that utilises the Treepl platform.
While Treepl withstood all other tests, the platform failed the portion of this test with regards to malicious file uploads. While file types are restricted within a promotion fulfilment form, the hacker was able to upload a permissible file type, then change the extension which then activates the malicious script file.
The Treepl team have advised they can fix this but requires a whole platform update, therefore they have asked for a public backlog request so the back end department can review and groom the update.
Please vote and accelerate this to action the update. The hackers will be retesting in February.